All around enterprise security Build apps to HIPAA & PCI standards Strong access control measures including TOTP and HOTP Two Factor Authentication Controlling access | 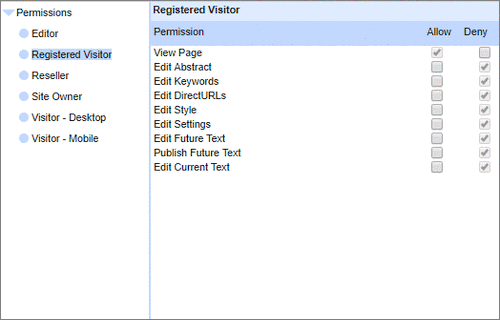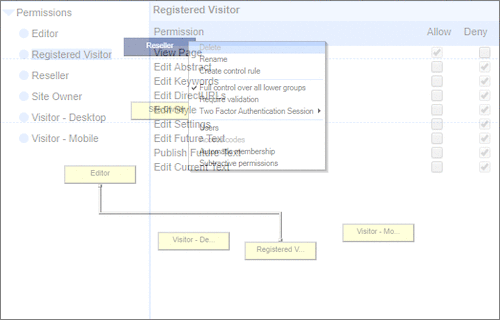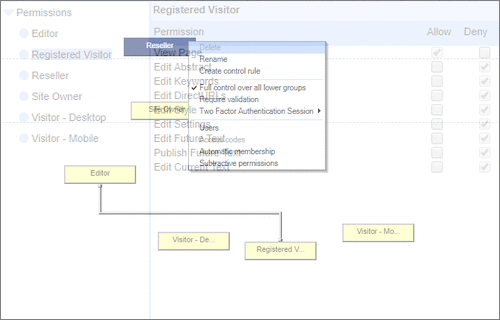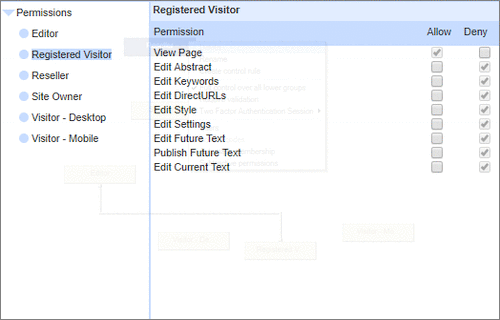 Personalized delivery & accessRobust fine grained user controls and permissionsEvery component has the fine grain user access control that is essential in commercial projects. The User Group Manager controls enable users to be in multiple user groups to 'slice-&-dice' controls and control hierarchies. Managing different views for Intranet, Visitor or Registered Customers is straightforward and does not need ongoing IT department involvement. |
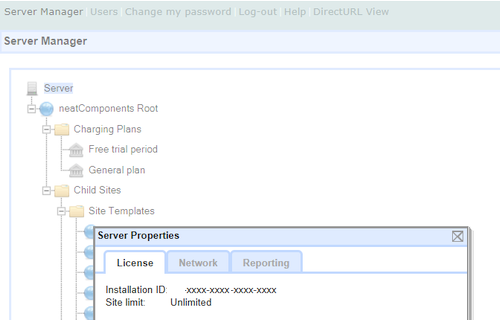 Data sovereigntyTake control over deployment location“Many countries have laws that require data to stay within their borders or even within the walls of a company. Firms want to use data but, worrying about leaks, often prefer to keep their own information inhouse.” The Economist. clearString gives you the choice of hosting on premises, or in a private cloud, or in the public cloud. And should you need, moving from one to another is a simple hassle-free process. clearString is also available as a Cloud service. |
 Access control Access control
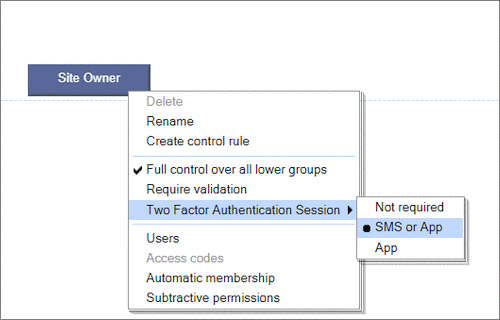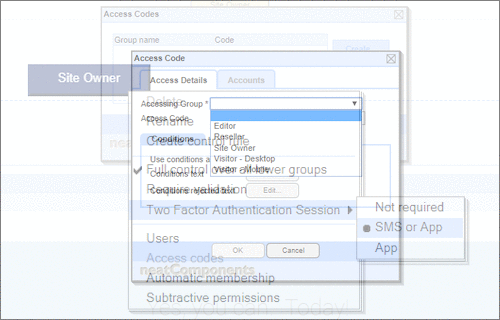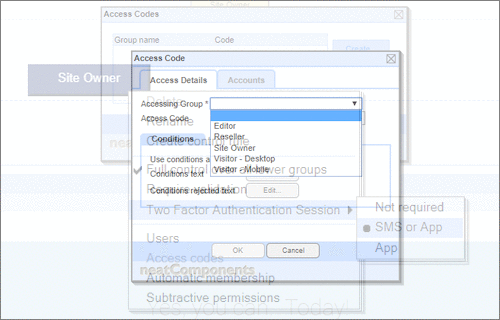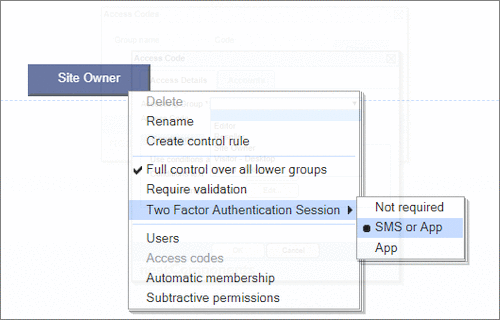
User Permissions and Two factor authentication.User Groups and Permissions enable you to quickly tailor the presentations to different users. Create Portals, Mobile versions, different language versions, or incorporate Affiliate and Associate schemes. Two Factor Authentication (2FA) is an additional level of security for applications and supports both HOTP & TOTP protocols. |
| Full enterprise security Build HIPAA & PCI apps TOTP & HOTP 2FA Controlling access Personalized delivery & access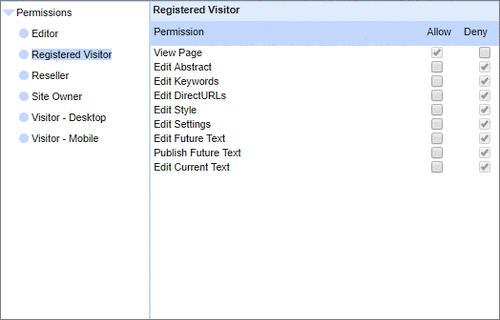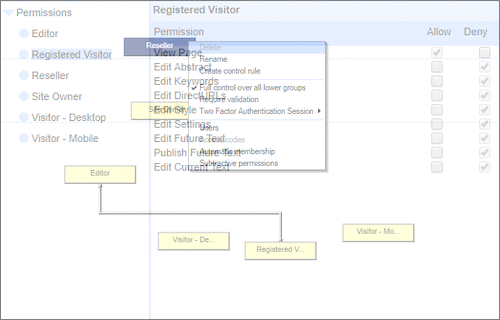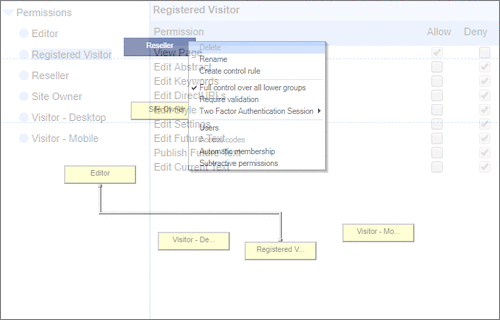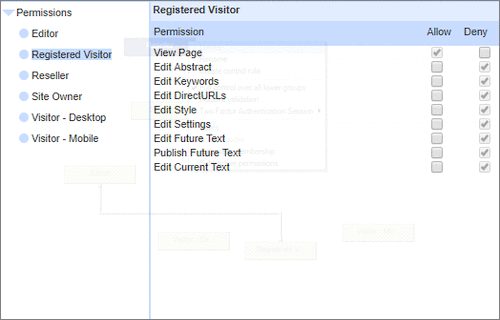
Robust fine grained user controls and permissionsEvery component has the fine grain user access control that is essential in commercial projects. The User Group Manager controls enable users to be in multiple user groups to 'slice-&-dice' controls and control hierarchies. Managing different views for Intranet, Visitor or Registered Customers is straightforward and does not need ongoing IT department involvement. Data sovereignty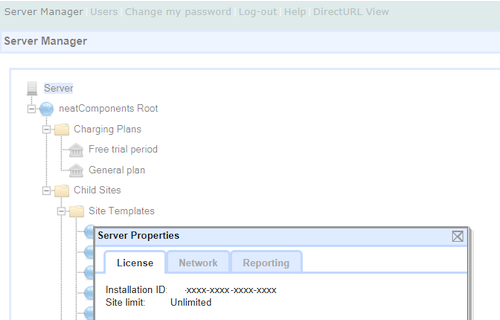
Take control over deployment location“Many countries have laws that require data to stay within their borders or even within the walls of a company. Firms want to use data but, worrying about leaks, often prefer to keep their own information inhouse.” The Economist. clearString gives you the choice of hosting on premises, or in a private cloud, or in the public cloud. And should you need, moving from one to another is a simple hassle-free process. clearString is also available as a Cloud service. Access control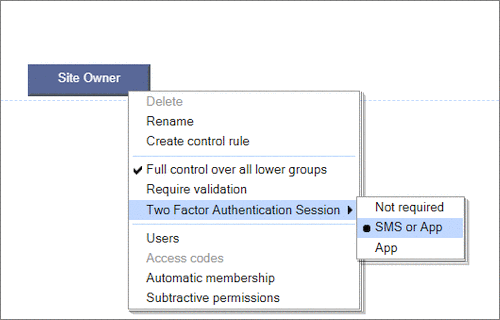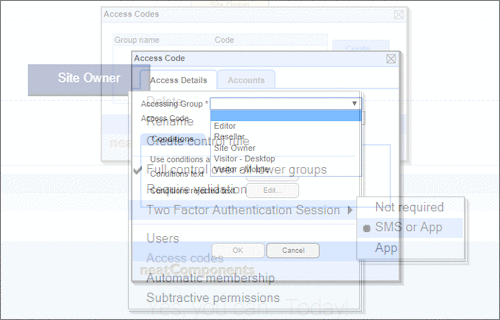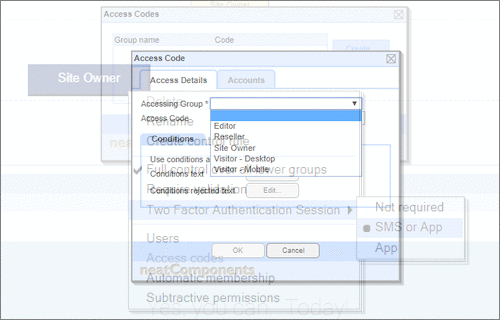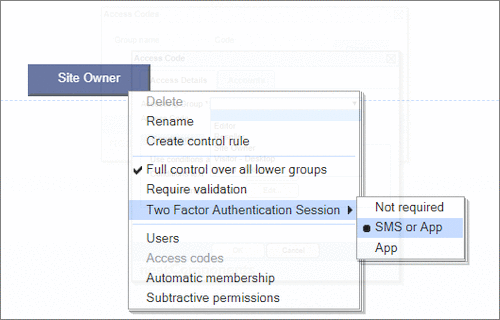
User Permissions and Two factor authentication.User Groups and Permissions enable you to quickly tailor the presentations to different users. Create Portals, Mobile versions, different language versions, or incorporate Affiliate and Associate schemes. Two Factor Authentication (2FA) is an additional level of security for applications and supports both HOTP & TOTP protocols. | All around enterprise security Build apps to HIPAA & PCI standards Strong access control measures including
TOTP and HOTP Two Factor Authentication Controlling access Personalized delivery & access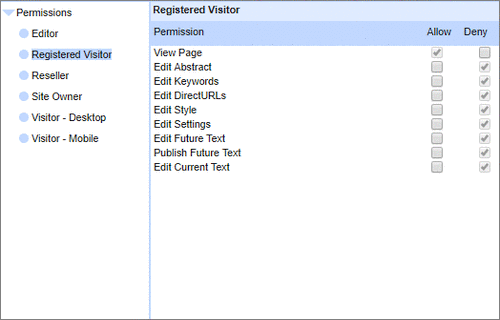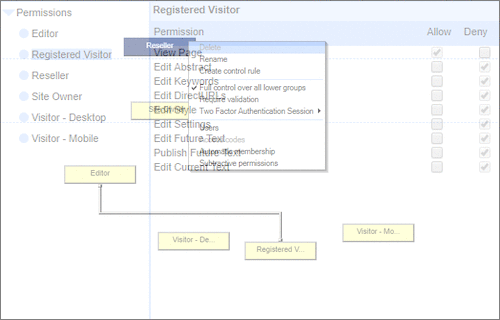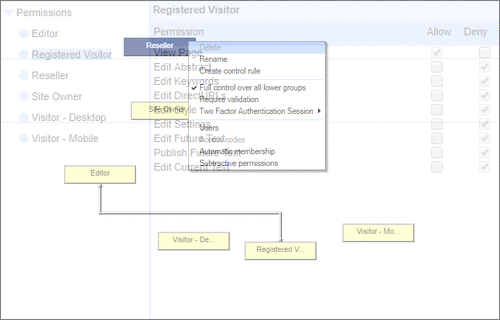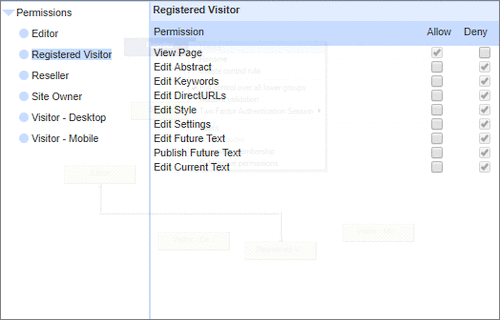
Robust fine grained user controls and permissionsEvery component has the fine grain user access control that is essential in commercial projects. The User Group Manager controls enable users to be in multiple user groups to 'slice-&-dice' controls and control hierarchies. Managing different views for Intranet, Visitor or Registered Customers is straightforward and does not need ongoing IT department involvement. Data sovereignty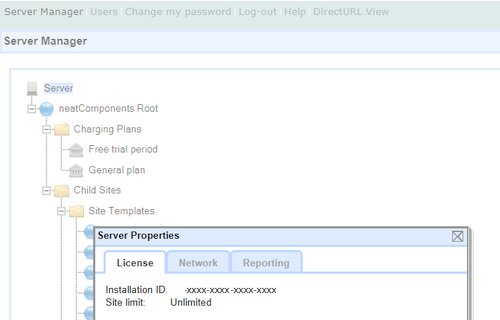
Take control over deployment location“Many countries have laws that require data to stay within their borders or even within the walls of a company. Firms want to use data but, worrying about leaks, often prefer to keep their own information inhouse.” The Economist. clearString gives you the choice of hosting on premises, or in a private cloud, or in the public cloud. And should you need, moving from one to another is a simple hassle-free process. clearString is also available as a Cloud service. Access control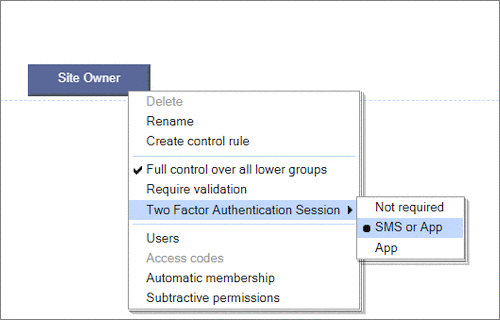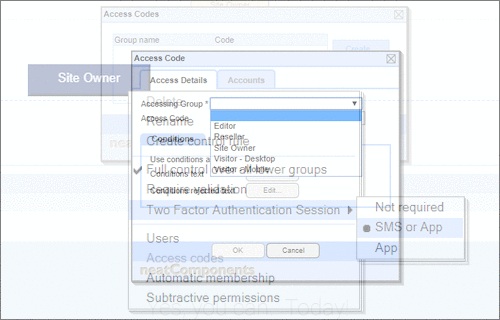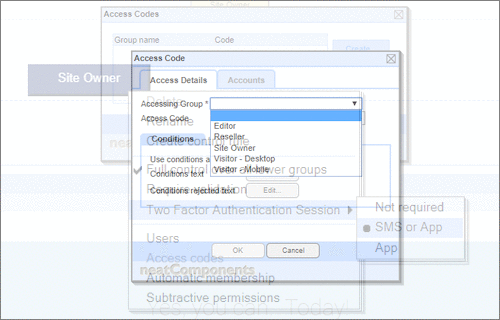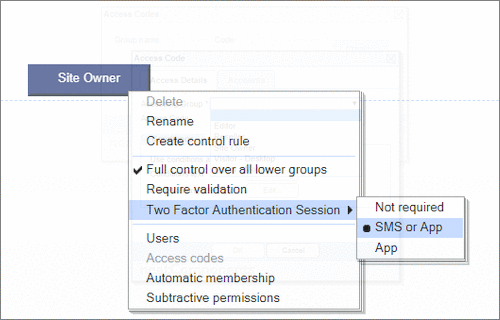
User Permissions and Two factor authentication.User Groups and Permissions enable you to quickly tailor the presentations to different users. Create Portals, Mobile versions, different language versions, or incorporate Affiliate and Associate schemes. Two Factor Authentication (2FA) is an additional level of security for applications and supports both HOTP & TOTP protocols. |
|
|
